4.9:Fundamentals of communication and networking
1 Internet Security
Firewall
- A firewall is simply a program or hardware device that filters the information coming through the Internet connection into your private network or computer system.
- A firewall uses one or more of three methods to control traffic flowing in and out of the network:
Packet filtering - Packets are analysed against a set of filters: IP addresses, protocols and port numbers. Packets that make it through the filters are sent to the requesting system and all others are discarded.
Proxy service - Information from the Internet is retrieved by the firewall on behalf of other systems and then sent to the requesting system, and vice versa. This creates a single point that allows monitoring entire network packets, easy error detection, attack detection and validity checking.
Stateful inspection - Stateful inspection monitors communications packets over a period of time and examines both incoming and outgoing packets. Outgoing packets that request specific types of incoming packets are tracked and only those incoming packets constituting a proper response are allowed through the firewall.
Symmetric and Asymmetric (private/public key) encryption
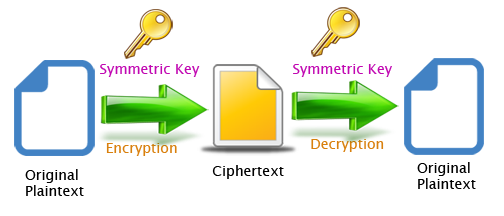
- Symmetric encryption
- The key used to encrypt and decrypt a ciphertext is the same. Caeser cipher is an example of symmetric encryption.
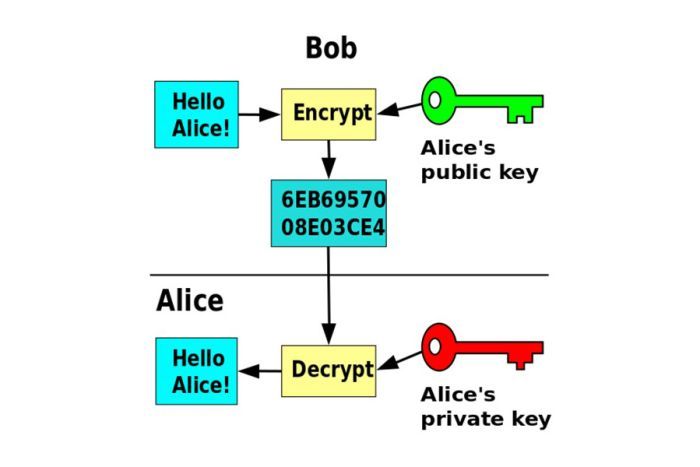
- Asymmetric encryption AKA public key encryption
- A part of public key infrastructure (PKI)
- A public and private key pair are generated such that although the public key is used to encrypt a message, only the private key will be able to decrypt it or vice versa.
- A sender uses the reciever's public key (visible to the world) to encrypt a message.
- The receiver then used his/her own private key to decrypt the ciphertext.
Digital certificates and digital signatures
- Digital Cerificates
- A
digital certificate is an electronic identity proof.
- The purpose is to verify the trustworthiness of message sender/websitesthat.
- A public key infrastructure (PKI) is a set of roles, policies, and procedures needed to create, manage, distribute, use, store, and revoke digital certificates and manage public-key encryption.
- Digital certificates are typically issued by a certificate authority (CA), which is a trusted third-party entity that issues digital certificates for use by other parties.
- A digital certificate is forgery resistant and can be verified because it was issued by an official, trusted agency.
- A certificate contains:
- the name of the certificate holder
- a serial number
- expiration dates
- a copy of the certificate holder's public key (used for encrypting messages and digital signatures)
- the digital signature of the certificate-issuing authority (CA) so that a recipient can verify that the certificate is real.
- Digital Signature
- Digital signature is a digital code (generated and authenticated by public key encryption) which is attached to an electronically transmitted document to verify its trustworthiness and the sender's identity.
- PKI requires the provider to use a mathematical algorithm to generate two long numbers, called keys. One key is public, and one key is private.
- When a signer electronically signs a document, the signature is created using the signer’s private key, which is always securely kept by the signer.
- The mathematical algorithm acts like a cipher, creating data from the document, called a hash, and encrypting that data. The resulting encrypted data is the digital signature.
- The signature is also marked with the time that the document was signed. If the document changes after signing, the digital signature is invalidated.
- When the signed document recieved, the signature is decrypted using the sender's public key to produce a hash.
- The recieved document is hashed using the same hash algorithm as the signer to produce a second hash.
- If the two hash values are identical, then the document is authentic.
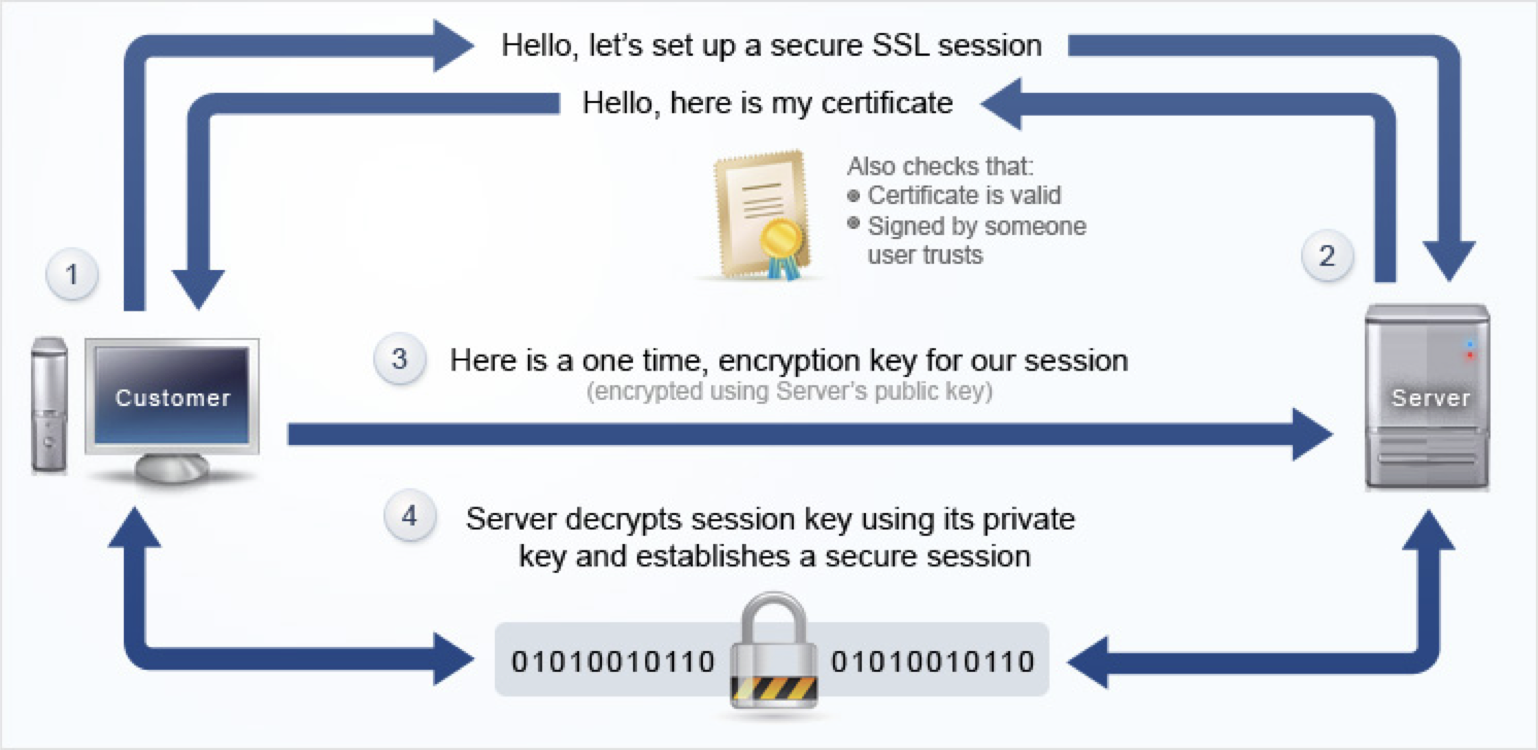
- SSL (secure socket layer), https (http secure)
- Secure Sockets Layer (SSL) was the most widely deployed cryptographic protocol to provide security over internet communications before it was preceded by TLS (Transport Layer Security). But people still refer it as SSL.
- https follows this protocol
- The diagram below shows the application of certificate, asymmetric and symmetric key encrytpion together in https.
Worms, trojans and viruses, and the vulnerabilities that they exploit
A computer worm is a self-replicating computer program that penetrates an operating system with the intent of spreading malicious code. Worms utilize networks to send copies of the original code to other computers, causing harm by consuming bandwidth or possibly deleting files or sending documents via email, or consuming too much system memory (or network bandwidth), causing Web servers, network servers and individual computers to stop responding.
A computer virus attaches itself to a program or file enabling it to spread from one computer to another, leaving infections as it travels. Almost all viruses are attached to an executable file, which means the virus may exist on your computer but it actually cannot infect your computer unless you run or open the malicious program.
Trojans or Trojan Horses will appear to be useful software but will actually do damage once installed or run on your computer. Those on the receiving end of a Trojan Horse are usually tricked into opening them because they appear to be receiving legitimate software or files from a legitimate source.
- Trojans can cause serious damage by deleting files and destroying information on your system. Trojans are also known to create a backdoor on your computer that gives malicious users access to your system, possibly allowing confidential or personal information to be compromised.
- Trojans do not reproduce by infecting other files nor do they self-replicate. They require human action to run,