TCP-IP
Table of Contents
1 TCP/IP
The Basics
- TCP/IP aka Transmission Control Protocol/Internet Protocol, is a suit of protocols governing how devices communicate with each other on the Internet or over networks
- TCP and IP are two separate network standards that make the internet possible.
- The Internet Protocol (IP) defines how
computerscan transmit data to each other. - The Transmission Control Protocol (TCP) defines how
applicationscan create reliable channels of communication across an IP network. - IP governs addressing and routing (more later)
- TCP governs how to maintain a reliable communication channel.
The TCP/IP Stack
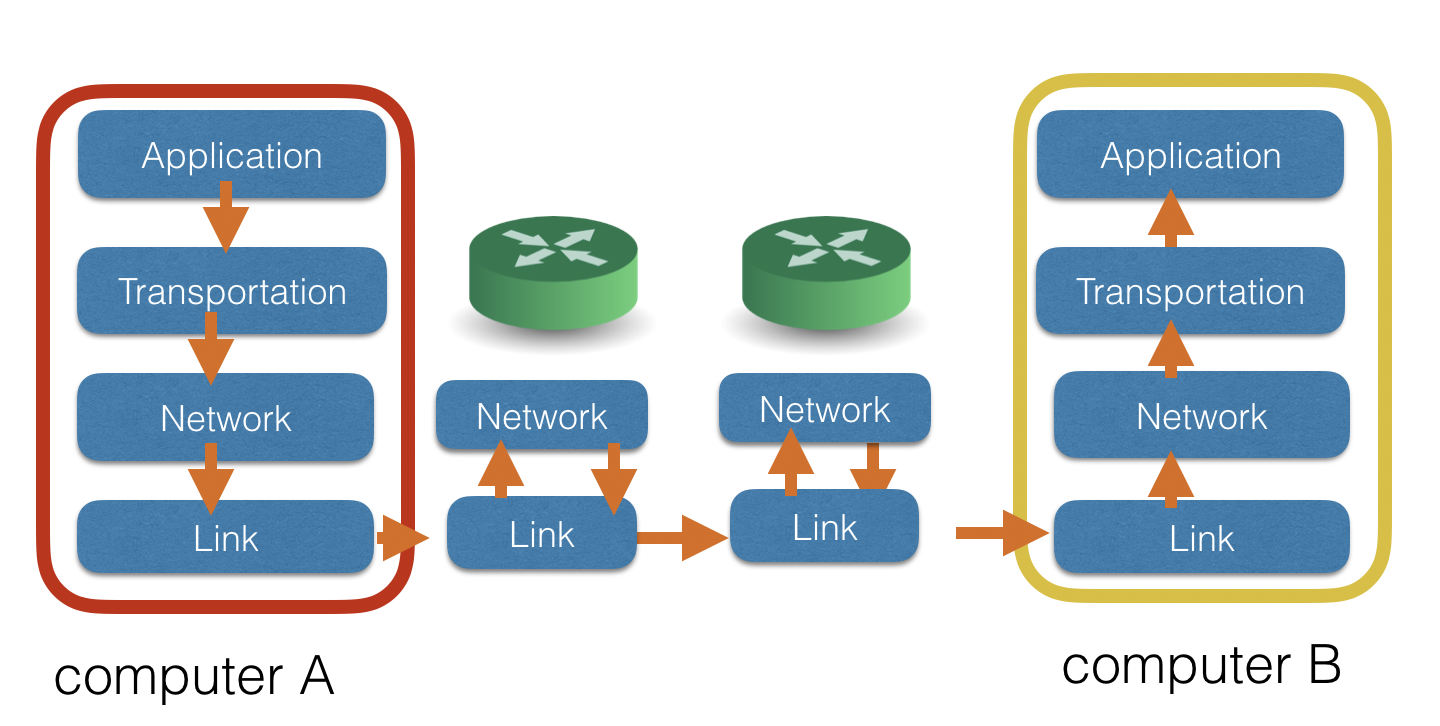
- The TCP/IP stack defines the 4 functional layers: each layer defines how the different software and hardware components involved in a network communication, together passing incoming and outgoing data packets down and up the layers.

- Each layer has a particular function in the data transmission:
Application layer: where applications such as a web browser or a mail client initiate communications by using specific protocols: http for web browser, pop3, imap, smtp for mail, or ftp for file transfer.Transport layer: where TCP protocols used to have create an end-to-end communication channel with recipient; split data into packets; assign port numbers to a connection channel; if packet lost, re-send; and acknowledge of packet arrival.a port numberis a logical number that identifies a specific process or a type of network service (more later). A device may only have on IP address but it can have many port numbers assigned to different processes, for example, a port number for web browser that connected to www.bbc.co.uk, another port number for the same web browser but connected to www.youtube.com.Network layer: where IP protocols used to identify source and desctination IP addresses; combiningIP address and port number, asocketis created for a communication channel.Link layer: where devices' physical connections are identified as all network communication are eventually sent and received through devices' NICs. Each NIC has a globally unitMAC (Media Access Contro) Address.
- When two devices communicate, the 4 layers work together passing incoming and outgoing data packets down and up the layers, down the layer from the sender and up the layer at the receiving end.
- When the channel crosses networks, routers are involved and routers only need to handle the network and link layer tasks. Can you explain why routers only need to work on the network and link layers?
Ports - Well-known Ports and Client Ports
- A
portis an endpoint to a logical connection - A
portis also the way a client program specifies a specific server program on a computer in a network Port numberranges from 0 to 65535- Port numbers from
0 to 1023are reserved ports for privileged services. Those port numbers are well-known ports. For example, you connected to a webserver on port 80 (http) or port 443 (https) by default. You can think well-known ports as the contact end point used by the server process so clients know where to connect to the server on a particular host. - The rest of the port numbers are known as
client ports- they can be assigned dynamically or statically to clients to connect to other services or to servers that may not intended to be known publically. - Here is a list of well-known ports where well-known application protocols use:
| Port | service | Description |
|---|---|---|
| 21 | FTP | File Transfer protocol |
| 22 | SSH | Secure Shell |
| 23 | Telnet | remote login |
| 25 | SMTP | Simple Mail Transfer Protocol |
| 53 | DNS | Domain Name System |
| 80 | HTTP | Hypertext Transfer Protocol |
| 110 | POP3 | Postoffice Protocol V3 |
| 443 | HTTPS | Hypertext Transfer Protocol Secure |
| 547 | DHCP | Dynamic Host Configuration Protocol |
The Roles of Sockets
IP address + port number = socket- A socket is a unique connection end point.
- Use web browser as an example, when you connect to www.bbc.co.uk on your computer say your computer has an IP address 123.45.66.78, your web browser assigns an available port number 4555 to this connection, therefore it has created a socket
123.45.66.78:4555to connect to www.bbc.co.uk which has a default port number 80 on http or default port number 443 on https. When you have received pages back from www.bbc.co.uk, those pages then being sent to that socket so you actualy get what you want to browse. - If you use the same computer with the same IP address connects to a different web site say www.youtube.com at the same time, another unique port number, say 5555 will be created for this connection, therefore, a total new and unique socket is created:
123.45.66.78:5555for you to communicate with youtube website.
The Roles of MAC addresses
A media access control address (MAC address)of a device is a unique identifier assigned to anetwork interface controller (NIC).- At the link layer, MAC addresses are changed at each hop. The source MAC is the address of the device sending the packet for that specific hop and the same for the receiving MAC.
- Unless two computers are on the same network, the initial destination MAC address will be the first router that packet is sent to.
2 Standard Application Layer Protocols
- On the top of the TCP/IP stack, there are application protocols that specifies the standard communications rules and interface methods used by hosts in a network.
FTP: File Transfer Protocol.- Used to download and upload files between ftp client and server.
- It can use anonymous and non-anonymous access
HTTP: Hypertext Transfer Protocol.- Used to comunicate between web clients and web servers.
- Web server's role is to serve up webpages in text form
- Web client's role is to retrieve webpages and webpage resources and render them accordingly.
HTTPS: Hypertext Transfer Protocol Secure.- Used to comunicate between web clients and web servers over encrypted channels.
POP3: Postoffice Protocol Version 3.- Used for mail clients to download email from email servers to a single device. Once emails downloaded from a server, it deletes it from the server.
SMTP: Simple Mail Transfer Protocol.- Used for
sending emailfrom email clients to servers - And used for
sending emailsfrom email servers to the correct destination mail servers
- Used for
SSH: Secure Shell.- Used for remote login to servers securely
- And for executing commands remotely and securely
- SSH client makes a TCP connection to a remote port for sending commands to this port using application level protocols such as GET for HTTP, SMTP commands for sending email
Examples of SSH
ssh user1@server1 The ssh client will login to a server called server1 remotely via command line. ssh user1@server1 'command1' The ssh client will authenticate to server1 using user name called user1 and run a command called command1 without the need to login to the server.
3 IP Addresses
IP address standards
An IP addressis- Internet Protocol Address
- A unique address assigned to a network device
- Made of 4 blocks of 3 digits, each block has a value from 0-255 which means 8-bit in each block, and total of 32 bits
- Use IPv4, there are about 4.2 billion (232) unique IP addresses globally.
- Computers and network devices use IP addresses to send and route data
- Certain addresses and ranges are designated by the IANA as reserved IP addresses.
192.168.1.4
- Since the Internet commercialisation in the 1990s, 4.2 billion IP addresses is quickly running out. A new addressing scheme was needed.
IPv6is the new standard for identifying devices on the Internet. It uses 128 bits.- Both IPv6 and IPv4 are being used currently in the Internet.
IPv6is normally expressed as 8 16-bit groups in hex:2001:cdba:0000:0000:0000:0000:3257:9652
Public and Private IP addresses
- The Internet Assigned Numbers Authority (IANA) is a function of ICANN, a nonprofit private American corporation that oversees global IP address allocation
- Some IP addresses have been reserved as private IP addresses
- Private IP addresses cannot be reached from outside their network
- Those private addresses are called "non-routable" addresses
- Here are the ranges of IPv4 private addresses:
10.0.0.0 to 10.255.255.255 172.16.0.0 to 172.31.255.255 192.168.0.0 to 192.168.255.255
- In your home network, you will see the 192.168.x.x IP addresses while at school you will see the 10.x.x.x IP addresses.
- If your computer has a private IP address, computers outside your network cannot directly connect to you. Your IP address is only unique in that network.
IP Address Structure and Network Mask
- An IP address has two parts: a network and a host identifier part.
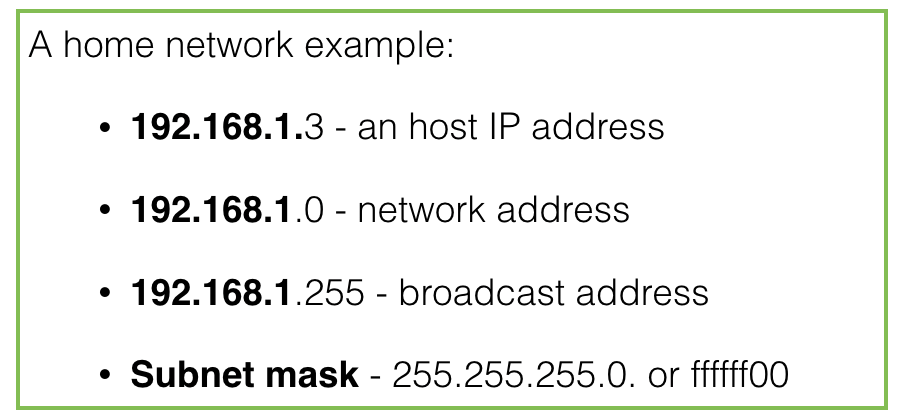
- In the following example, the 192.168.1.0 is the network address while the 3 is the host identifier
- The subnet mask is a bit pattern to indicate which bits in the IP address are used for the network address
- The subnet mask 255.255.255.0 indicates that the first 24 bits are used to identify the network address, and the last 8 bits used to identify hosts on the network
- Therefore, to work out the network address from IP address, you use AND logic operation:
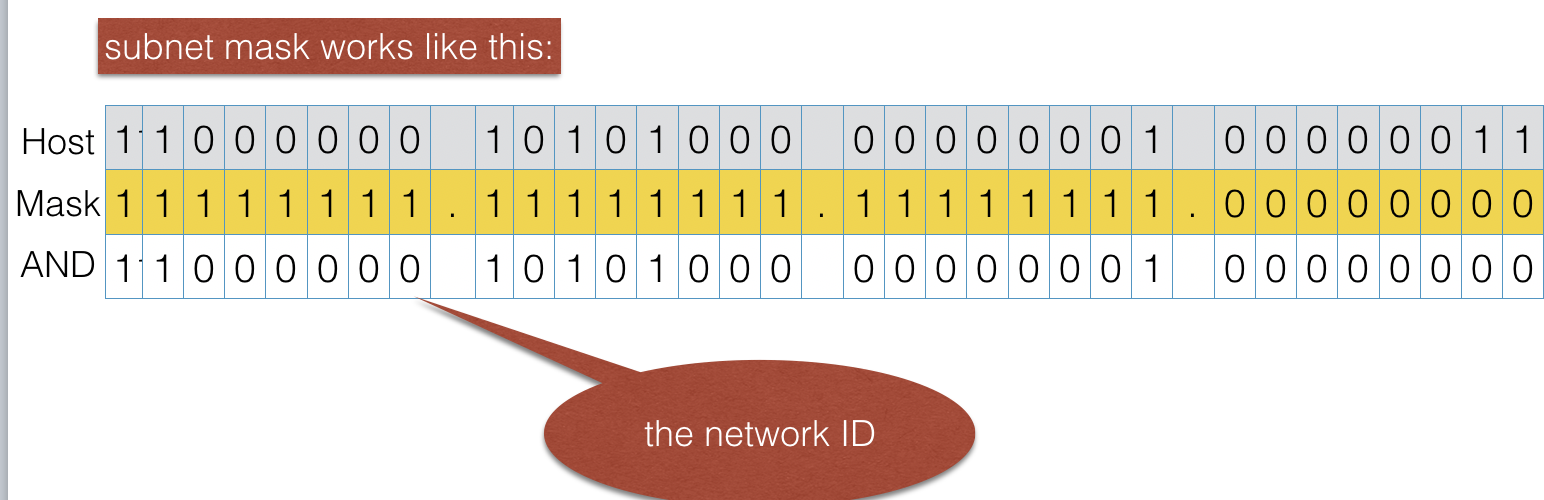
- To decide if a destination IP address is within network or outside network, the sending host performs the following steps:
- Perform AND logic operation on its own subnet mask and destination IP address to produce a network ID
- Perform AND logic operation on its own network mask and its own IP to produce another network ID
- If the network IDs are not the same, which means the destination IP address is on a different network, the sending host must send the data to a router for forwarding
Network Address Translation - NAT
- NAT is needed for primary two reasons:
- Due to limited routable IP addresses, private/non-routable IP addresses can still us NAT to communicate with hosts outside its network
- Better security can be achieved since the private IP addresses are never visible to the outside world
- a NAT application (Router, Firewall) works as following:
- changing the source address (private IP address) on every outgoing packet from the internal computers into the single public IP address.
- a different source port is assigned for packets coming from each computer, so that while the packets return with a single public IP address, it can still remember which packet needs to go to which computer by port mapping
- returned packets are re-assigned with its respective private IP address of the computer it needs to go to and the public IP address is discarded by the NAT application
- Here is a wonderful video on NAT
4 DHCP - Dynamic Host Configuration Protocol
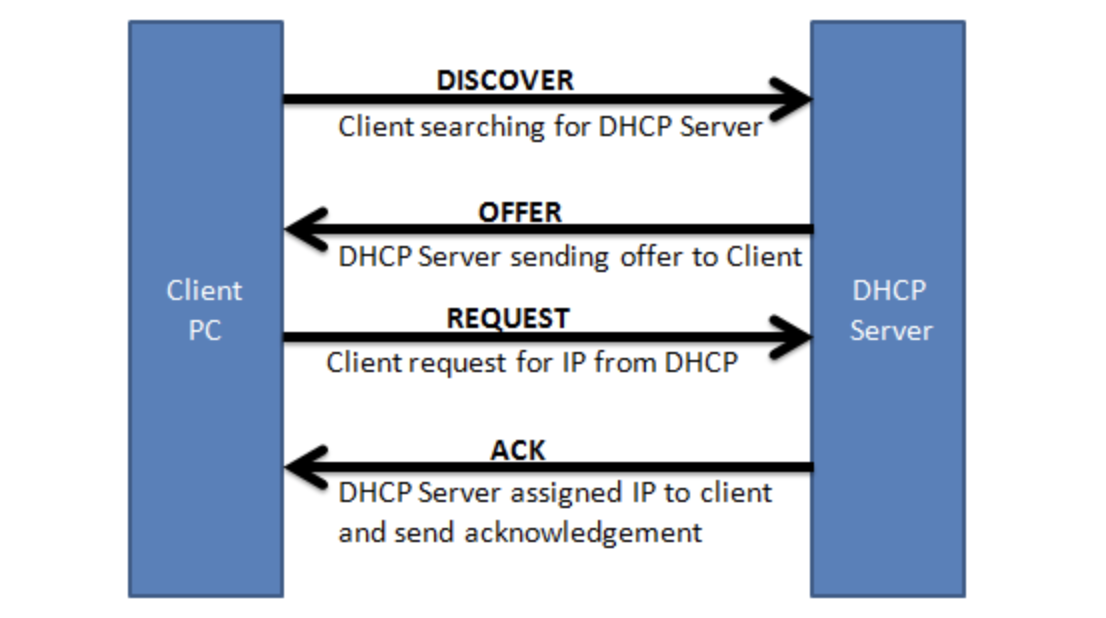
- When a host joins in a network, it needs to obtain an unique IP address in order to communicate with other hosts
- This process of obtaining an IP address is done on the application layer using DHCP - Dynamic Host Configuration Protocol
- In a nutshell, DHPC uses client-server model - a client requests an IP, a DHCP server leases an IP address to the client
- The protocol works as below:
5 Port Forwarding
Port forwardingis needed when a machine on the Internet needs to connection to a machine that's behind a firewall or NAT router.Port forwardingredirects a communication request fromone addressandport numbercombination(socket) to another while the packets are passing a network gateway, a router or firewall.Purpose of Port forwarding:- It allows remote computers to connect to a specific computer or service within a private local-area network
- Here is a video illustrating how port forwarding works in some detail:
6 Client Server Model
The Basics
A model of computingthat involvesa server, normally an application that runs on a host computer or workstation, performance some actions on the server and then sends responses to a client.a client, normally an application that runs on a personal computer or workstation, sends requests to a server and relies on a server to perform some operations then receive a response.
- Examples of client server model include:
- web server that serves webpages
- web client requests webpages form web servers
- DHCP client requests an IP address
- DHCP server serves an IP address upon client's request
API - Application Programming Interface
- A set of rules/protocols specifying how two applications interact, specifically, the format of requests and responses between a server and a client
- Example 1, using a Clarifai API to interact with the Clarifai AI server
- Example 2: using Google client API to interact with youTube server
- Example 3: using MET office’s DataPoint API to get weather data for your own website
Websocket Protocol
- WebSocket is an API for the web client to interact with a web server. It specifies:
- a computer communications protocol, providing full-duplex communication channels over a single TCP connection.
- a persistent connection between client and server, allowing both parties to send data at any time.
- this allows for fast, real-time and interactive communications.
- a much less over head for the server.
Web CRUD Applications and REST
CRUD: Create, Retrieve, Update, DeleteREST: Representational State Transfer.RESTis a system design that: (AKA, Restful)- Allows the use of HTTP methods (POST, GET, DELETE, PUT) to interact with databases via a web server.
- allows for separation of client and server to be updated and developed independently of each other
- Clients do not need to know how the server is going to fulfil the requests
- REST enables CRUD to be mapped to database functions
- The function mapping as follows:
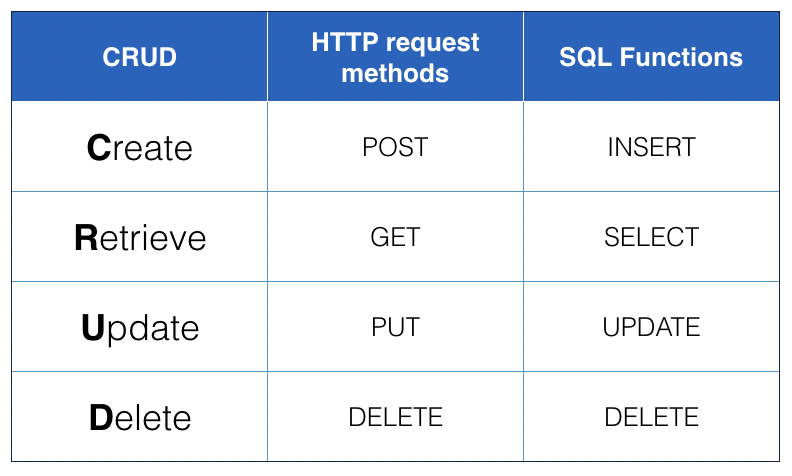
- In a nutshell,
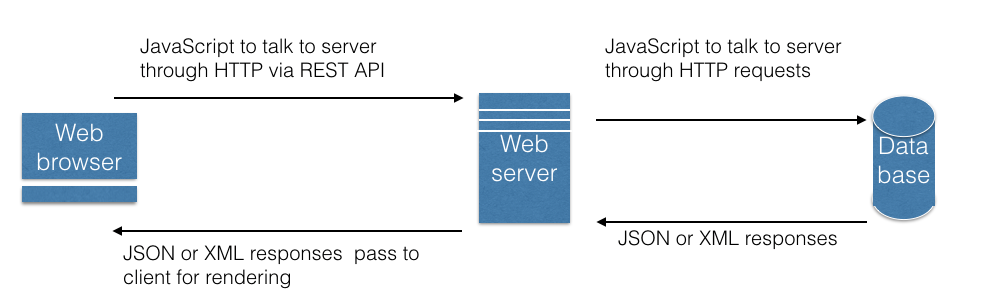
RESTworks as following:- REST API created and runs on server
- client browser runs Javascript (referenced by HTML files) which calls REST API using HTTP methods
- JSON (JavaScript Object Notation) or XML can be used to transmit data between a server and web application
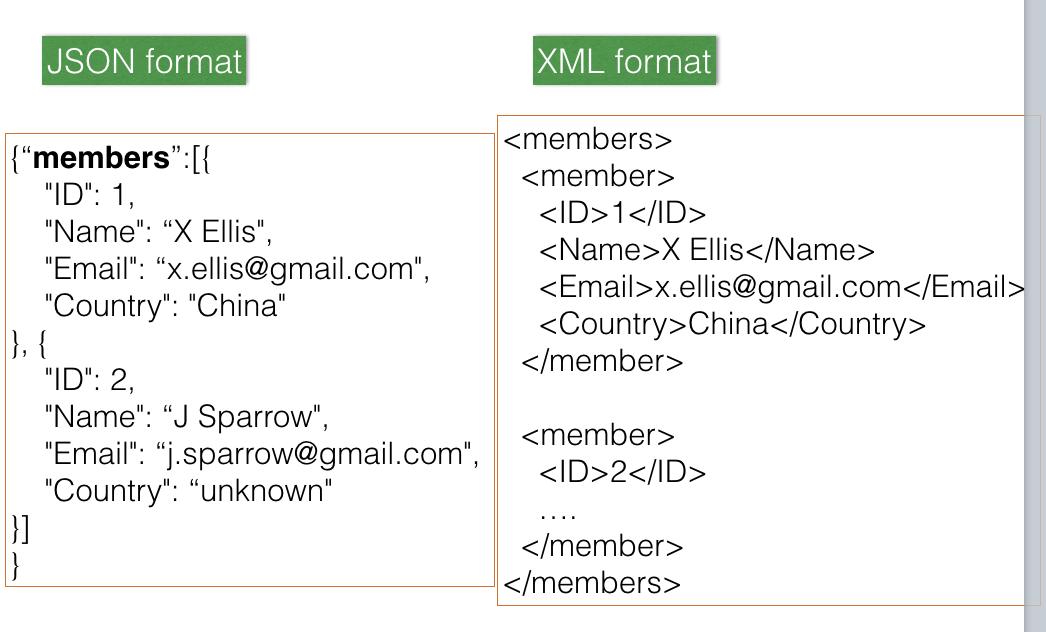
JSON and XML
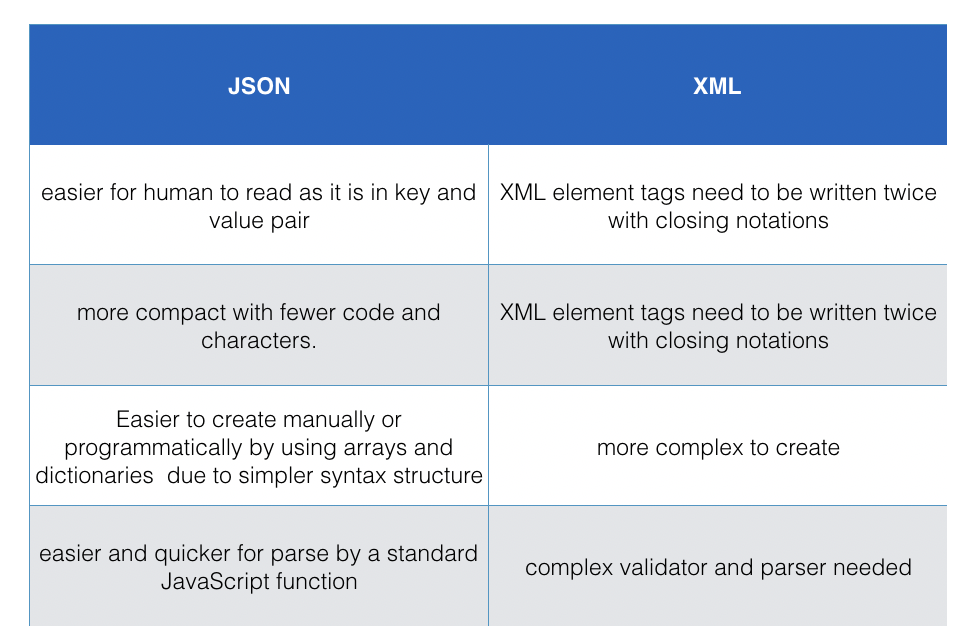
- JSON arrived later than XML, but gaining popularity as it has many advantages than XML.
- Examples of JSON and XML:
- Comparison of JSON and XML:
7 Thin and Thick Client Computing
Thin Client
"A thin client is a lightweight computer that has been optimized for establishing a remote connection with a server-based computing environment. The server does most of the work, which can include launching software programs, performing calculations, and storing data" - wikipedia
- Thin client is type of client that is small and light weight
- The server does most or all of the data processing therefore server must have multiple processors or a lot of RAM
- The client can be just a terminal that connected to a server
- Client's operating system loaded from server at boot this means higher bandwidth network connection required and network must use switch not hub
- UI rendered and sent to terminal
- Clients will only need slower processor or reduced RAM or no HDD
- Examples of thin client applications include web-based application which can be accessed on the internet using a browser, such as Google docs. These types of applications do not require any installation of software on the client side.
Thick Client - or Fat Client
- This type of client performs the bulk of the processing on local PC
- It needs resources for those processing
- Clients render UIs locally, therefore, more processor power, more RAM and more HDD needed on clients
- Skype and most game consoles are fat clients
Thick and Thin
- A fat client still requires at least periodic connection to a network or central server, but is often characterised by the ability to perform many functions without that connection.
- In contrast, a thin client generally does as little processing as possible, relying on access to the server each time input data needs to be processed or validated.